After reading this article, you will know the five elements of the NIST CyberSecurity Framework (CSF) and why they are important for your business. NIST released its latest CSF in 2018, and it serves as a guide to how to approach cybersecurity from a holistic perspective.
In a world where so much misinformation thrives (on any topic), IT security is no exception. Business owners tend to think they are “secure” if they use multifactor authentication. Or they think if they have a sophisticated firewall, they are safe. The reality is that every business is different. Since they are different, every business needs its own unique plan and approach to security. The NIST CSF provides businesses some structure in the security process.
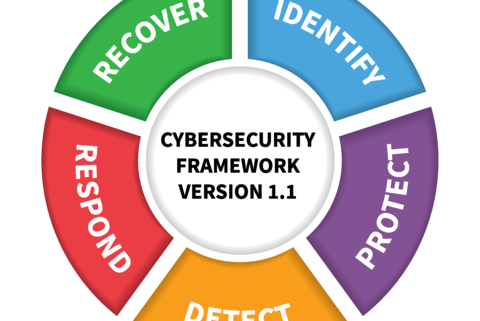
NIST has broken out the framework into five elements: Identify, Protect, Detect, Respond, and Recover. These five elements are activities that need to be performed in order to appropriately approach cybersecurity for any organization. While these activities use familiar terms, there is more than meets the eye for each one. Here is a breakdown of each element:
1. Identify
This seems simple enough at first glance, but start pealing back the onion, and you find many layers to this one element. Simply put, the Identify piece of the puzzle includes both inventorying and risk analysis. In the inventorying piece, you are identifying your mission critical assets – both material (devices, including virtual) and intellectual (IP). Once you have identified those assets, you perform a risk analysis to determine where you are exposed.
2. Protect
Along a similar vein, the Protect element seems straightforward as well, but there are some aspects to protection that complicate it. For instance, you aren’t simply protecting your data and assets from attacks, you are also working to protect the organization by mitigating successful attacks. You also need to include your personnel in the protect element. What training needs to be implemented in order to mitigate the threat of user hacks? What specific security awareness training exercises will benefit your personnel the most? Those are some of the questions you will be asking in the Protect exercise. The main idea is protecting your critical assets and mitigating the ill effects of successful attacks.
3. Detect
Detect is ongoing and active. How will you know if you are being attacked? Various studies show that many times hackers successfully attack businesses without them even knowing it. The business doesn’t realize they’ve been compromised until the hackers use their access to negatively impact that business. This means that for every mission-critical piece (both intellectual and property) there needs to be a detection mechanism to alert when hackers are trying to compromise each system. Most organizations do not have this piece in place at all.
Another aspect of the complexity with regard to detection is the constantly moving target of patching (both operating systems and third-party software). Staying on top of the latest security patching while verifying that these patches don’t introduce bugs or other unintended consequences requires diligence and commitment. IT personnel must create security baselines and monitor against drifting away from those baselines. Doing so is easy to overlook, especially in environments where IT personnel are constantly resolving end user issues.
4. Respond
The Respond element is tied to the Detect element. Once your detection system alerts you to a compromise, how will you respond? Who is alerted? Every business needs to identify the person who will own this response. This doesn’t mean the activities of response can’t be delegated to other employees, or even a third-party MSP. This simply means that someone needs to be responsible for ensuring the response is appropriate and thorough.
What makes the Response element difficult is the variance of responses depending on what the detection system is alerting. Nevertheless, it is imperative that responses include the ability to audit the threat, mitigating the threat immediately, implementing controls to ensure the threat is contained, while keeping other mission-critical systems online and free from attack.
5. Recover
Recover is the simplest of the five elements. This is where you execute the failsafes you implemented in the Protect element. Again, someone in your organization must own this element and ensure that the recovery planning process is followed. You also need to ensure in your recovery planning process that you include a hotwash meeting post-incident to document lessons learned and refine your recovery process. IT personnel should schedule routine recovery exercises to test their effectiveness. When was the last time you performed a scheduled business recovery exercise?
Conclusion
NIST has identified these elements as the best approach to cybersecurity. While every business is different and each of these elements will impact businesses in different way, these elements serve to bolster the maturity and security posture of all businesses and organizations. If you skip any one of these elements, your business will suffer. Think of these elements as you would elements on the periodic table. We all know the elemental makeup of water is H20. Change or remove either element, and you no longer have water. You might even end up with something like hydrogen peroxide, for instance. In like manner, change or remove any one of the five elements in NIST, and you have something altogether different from “secure.”
If this framework seems overwhelming, TCS can help! We’ve built our processes around the cybersecurity framework to ensure we aren’t missing anything with regard to our clients’ security. We would honor the opportunity to help your organization, as well. If you want to learn more about these elements, stay tuned for more content coming with deeper dives into each one.

 Credit: N. Hanacek/NIST
Credit: N. Hanacek/NIST iStock
iStock