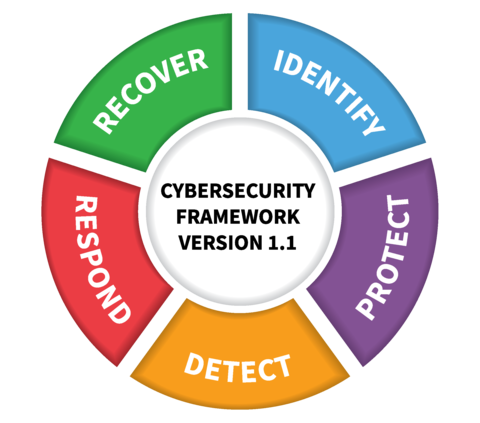
Continuing our NIST CyberSecurity Framework (CSF) series, the second function of the CSF is Protect. If Identify is the “what” of cybersecurity, Protect is the “how” of cybersecurity. As we will see in this article, the “how” of protection not only is complicated, but it also varies from organization to organization.
There simply is no one-size-fits-all approach to securing a business or organization. Your approach to cybersecurity depends upon the unique and specific devices your company utilizes, how those devices communicate, the layout of your office workers (local, remote, hybrid), the ways in which your users communicate between themselves, the location of your critical data, the use of cloud platforms and software as a service, and more.
There are five primary aspects to the Protect function:
1. Access Control and Authentication
Access Control and Authentication and be summed up as Identity Management. This is a fairly straight-forward concept – how do you know only authorized users have access to critical datasets? How do you know that when a user gains access to critical data, it is really the intended user? What technologies will you leverage to ensure that impersonators are not accessing your critical data?
How you answer those questions is where this aspect of the Protect function gets complicated. For instance, if you use a PIN (like an ATM code), you will have different policies and procedures for how to properly use PINs versus a company who chooses to leverage smart cards for identity management. Each of those solutions has different ramifications and implications for how to successfully use them. If you decide to leverage both technologies, you create even more complications. Now, multiply that times the various identity management tools and technologies possible, and you have an idea at just how complicated keeping track of all the technologies and ensuring they are utilized securely can be.
2. Security Awareness Training
The second aspect to the Protect function is Security Awareness Training. The easiest avenue for hackers in today’s world is the end user. We want our employees to be helpful and efficient when they are dealing with those outside our organizations. Hackers know this and they often are masters at using that helpfulness to their advantage.
Some things you need to consider when creating a security awareness training program for your users are:
- What needs to be included in the training material based on the needs and risks particular to your organization?
- Who will be responsible for performing the training?
- How often should the training be performed?
- What methods will be used to perform the training?
- How will you measure the success of the training for each employee?
- How will you measure the success of the training program over time and evaluate its effectiveness?
Once the training program has been outlined, then you must execute that training. After measuring the training for results and getting feedback from employees as to how the training can be improved, you must then make the necessary adjustments to enhance the training over time.
3. Data Security
Data security falls into the triad objective of Confidentiality, Integrity, and Availability. This triad over time has become known as the Security CIA triad (not to be confused with the Central Intelligence Agency). The principle is simple enough to grasp. You want your critical data to remain private (Confidential), you want to ensure that everyone who should have access to that data does (Availability), and you want to ensure the data is accurate and tamper-free (Integrity).
One of the primary ways data is protected is via encryption. Confidential data should be encrypted at all times – even when that data is in motion. It’s easy to encrypt data at rest, most storage platforms have those capabilities built in. The difficulty arises in tracking the various ways that data is accessed (internally, remotely, from a Cloud platform, etc.) and ensuring that the data remains encrypted at the appropriate levels during the transport from the datacenter to the end-user.
Finally, for those who have mobile devices (laptops, tablets, smartphones, etc.) in their workforce, you must have adequate levels of mobile device management. Some examples of features required for effective mobile device management are as follows: device location, remote wipe, remote lock, enforced encryption, enforced device idle timeout/lock, approved applications, and advanced logging.
4. Policies and Procedures
The general rule as it applies to policies and procedures is document, document, document! The more you can document concerning the different policies and procedures your company considered implementing and why those policies were/weren’t adopted, the better.
Security for any device starts at the configuration level, so be sure to document policies outlining configuration baselines and standards by which everything in your environment will be configured. You will need to review those baseline configurations and standards annually to ensure they remain up-to-date. These baselines not only include your workstations, servers, and endpoints. They also include your firewall/router, your wireless setup, your phone system configuration, and every other technology (both hardware and software) your organization uses to perform its business.
Once you have created policies and procedures for how each device and application is to be configured along with the hardware specifications required for such a configuration to perform efficiently, you will need to write policies and procedures for what your users can and can’t do. In those policies, you will want to include expectations of privacy (if any and to what degree), define what devices and applications are permitted for company use, define whether or not devices can be used for personal purposes, define how users will employ devices in a secure manner, etc. Again, the more specific you can be in these policies and procedures, the better.
5. Protective Technologies
The final aspect of Protect is working to ensure your policies, procedures, and agreements align with the implementation of your technical environment. This means, for instance, that you regularly analyze your VoIP phone system to ensure that your setup is aligned with your policies and procedures. This also means that you are auditing your wireless network setup to ensure it is properly secured. The same would be true of your endpoint devices, servers, switches, and firewalls. Finally, you will want to revisit your application whitelist to ensure it is updated, as well.
Conclusion:
As you can see from this post, to perform the Protect function of CSF, you will need to take a lot of things into consideration. You don’t have to start from scratch, however. While each organization and business looks different in the details, the starting point is often similar. TCS can help you analyze the standards and appropriate them to your specific business. We have experience across a broad range of industries and use cases that can help you save time building these policies and procedures.
Note: All the resources used for this article can be found at the following site: https://www.nist.gov/cyberframework/protect

 iStock
iStock
 Credit: N. Hanacek/NIST
Credit: N. Hanacek/NIST