Last week, we started our NIST CyberSecurity Framework (CSF) series with an introductory article. In that article, we outlined the five functions of the NIST CSF: Identify, Protect, Detect, Respond and Recover. This article will dive a little bit deeper into the first function – Identify.
Whenever we think about a holistic protection plan for anything, we need to start with the obvious – what needs to be protected, and what substructure needs to be in place to ensure its protection? That in essence is what the Identify function of the CSF seeks to accomplish.
There are six primary aspects to the Identify function:
1. Asset Management
Simply put, you can’t create an effective strategy to protect key assets without knowing exactly what assets exist to protect. This step requires creating and maintaining an active inventory of hardware and software. From the hardware perspective, this would include not only servers and workstations, but also network infrastructure (switches, routers/firewalls, wireless access points, etc.). Some larger organizations will use an asset tag to track hardware in the organization.
On top of the hardware, you also need to maintain an active inventory of software, as well. Most people think of operating systems when software is mentioned, but this instance of software would include third-party applications, such as Adobe Reader, Office Applications, and endpoint security. On the software side, you need to be able to identify what versions are being employed and whether those versions are properly patched and updated.
Be sure to include documented onboarding and offboarding policies for how IT should introduce new hardware and software into your environments. Your offboarding documentation needs to include any destruction requirements necessary to fulfill your regulatory obligations.
2. Business Environment
The business environment needs to be defined. What is the mission of the company? How is that mission going to be accomplished? Who are the stakeholders of that mission? How are the various activities of that mission going to be prioritized and assigned to employees? How are those activities going to be safeguarded against security threats? These are some of the questions that need to be answered in this subsection.
The Critical Success factors for this subsection are (1) Strong Upper-Level Management Support, (2) Practical Information Security Policies & Procedures, (3) Quantifiable Performance Measures, and (4) Results-Oriented Measures and Analysis. Here is a helpful visual from NIST 800-55:
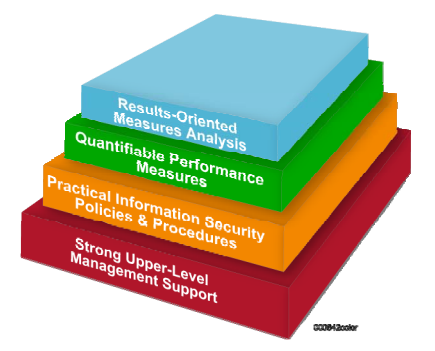
Notice that we start with the strong upper-level management. Upper-level management should not only provide a vision and a commitment to these objectives, they should model that commitment to everyone in the organization. So often, we see the CEO and other members of upper management trying to be the exception to the security rule. Be advised, upper-management, if you don’t take this seriously, your employees won’t either.
Also, take note of the emphasis on “practical” policies. If you don’t make security policies easy to follow, users will find ways to subvert and circumvent them. We see this regularly with users employing personal versions of Dropbox, personal email, and other means to avoid the hurdles of cumbersome security policies. Security done right is user-friendly and efficient, even when it’s not necessarily convenient.
Finally, security measures must be in place to quantify user adherence to those policies and procedures. Management should maintain goals and objectives surrounding these key security performance indicators. These performance metrics need to be analyzed and reported on a regular basis to ensure they are being met. Management should use these measurables to identify what further can be done to improve effectiveness and efficiency.
3. Governance
The management team of any organization must be involved in the governance of information security. This means they are the ones who create, enforce, and oversee the security policies and procedures of an organization. They also have a hand in choosing the support tools to deliver and enforce their security policies. Smaller organizations often employ third-party managed services providers to assist them in these areas, but the governance of them ultimately falls on management. In those instances, management holds the third party accountable for maintaining their security posture. Nevertheless, even though management isn’t actually doing the work, they are responsible for ensuring the work gets done via routine reporting evaluations back to management.
4. Risk Assessment
In order for a risk assessment to be successful, four components must be present: framing risk, assessing risk, responding to risk, and monitoring risk. The framing of risk simply is defined as determining the personnel who make risk-based decisions within the organization along with the context in which those personnel make risk-based decisions. The NIST 800-39 document includes a helpful diagram for this process:
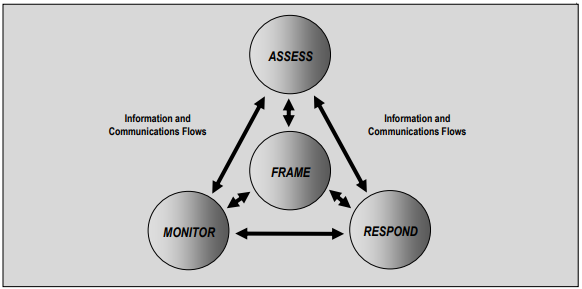
Once that risk context and the risk decisions have been framed, you need to delineate the boundaries around those decisions. Each risk frame exposes potential harm to the organization. The more adverse the impact of a decision, the more risk it carries. Typical risk assessments include a scoring matrix that accounts for cost/severity, percentage of likelihood, and the level of controllability. The composite risk score for each area is often rank ordered to help an organization prioritize their risk reduction efforts.
Note: Performing risk assessments should occur on a regular cadence appropriate for your organization.
5. Risk Management
Based on the scoring system of the risk assessment above, the next step is to respond by managing risks. There are a number of responses to risks: risk acceptance, risk avoidance, risk mitigation, risk sharing, risk transfer, and any combination of these responses. Be sure to document whatever response you choose for each particular risk. Finally, once you have documented the risk responses, management must formulate plans to implement those responses and monitor those implementations to ensure their overall effectiveness.
6. Supply Chain Risk Management
This might sound like a subset of Risk Management, but this aspect of the Identify function is a bit different. Instead of organizational risk management, this is a very specific kind of risk management. When you are a provider of communications products or employ those products in your company, you must guard against fraudulent counterfeits, tampered equipment, and the insertion of malicious software, firmware, or hardware from your vendors. This requires vetting the vendors for quality controls and manufacturing standards appropriate to the regulative requirements for your organization.
Some questions you might consider for this exercise are: Are these components manufactured and assembled in a hostile country? What is the chain of custody from the vendor to the end user? How does the manufacturer ensure their components are tamper-free upon arrival? Then, train your personnel how to inspect those items on arrival before you implement them into your IT environment.
Conclusion
As you can see, there are many facets to the Identify function within the CSF. Even then, this article simply scratches the surface. It’s not uncommon to feel overwhelmed by all this information. If this overview seems overwhelming, and you need a partner to assist you with your cybersecurity efforts, TCS would be honored to have a conversation with you about how we can help bolster your cybersecurity posture.
For a list of documents that informed this article, please see the following website: https://www.nist.gov/cyberframework/identify

