Continuing our series of the NIST CyberSecurity Framework (CSF), we now come to the Detect function. The Detect function is the simplest and most straightforward function within the CyberSecurity Framework. The work of this function is to create an Information Security Continuous Monitoring (ISCM) program. The NIST 800-137 publication is helpful for explaining the best process for creating and executing an ISCM for your organization.
Here are the six steps to building an effective ISCM as outlined in that document:
1. Define the ISCM strategy
A proper ISCM starts with the leaders of the organization. If the leaders do not take security seriously, it’s likely that no one else in the organization will see it as important either. What does it look like for leaders to take security seriously? The best way is for leaders to inform and shape the narrative of what information is important to the organization, what levels of risk they deem acceptable and unacceptable, and to engage with management and IT to develop appropriate risk governance policies and procedures to protect the organization.
Simply put, the leaders define the key performance indicators (KPIs) for security, along with the policies and procedures necessary to ensure the best outcomes possible with relation to those performance indicators. Naturally, the leaders will leverage input of from the rest of the organization to help them in this strategic process, but the responsibility of defining these key security performance indicators and governance policies falls on the leadership itself.
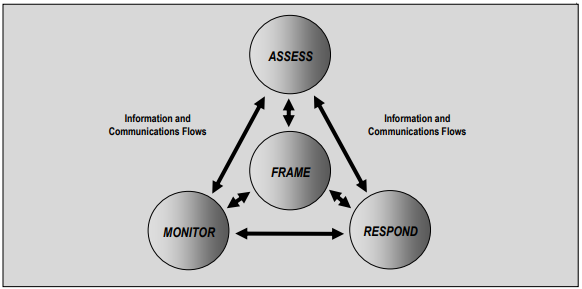
Here is a helpful diagram from NIST 800-137 illustrating how the entire organization should be involved in this process:

It’s important for the leaders of the organization to view the ISCM as an ever-evolving approach to securing the organization. Subordinates (Tier 2 and Tier 3) should regularly report back relevant data to the leaders (Tier 1) of the organization, so that policies and procedures can be updated for better efficiency, accuracy, and effectiveness. The security posture of the organization, thus, should improve continuously over time.
2. Establish your ISCM program
Once the leaders of the organization define the ISCM program, managers (Tier 2) of the organization should leverage tools to automate the data collection and sort data into digestible formats for review. The aim here is to develop the mechanisms by which data will be collected (automatically and/or manually) and how often that data will be reported back to the leaders of the organization. The leaders should maintain some sort of dashboard to actively monitor the key security performance indicators, so they are aware when security-related events are occurring within the organization.
Once managers establish the tools and mechanisms for monitoring and maintaining security KPIs, then they should define the metrics for how often IT will monitor and assess the data, how often that data gets updated to the leadership of the organization, and how often the mechanisms will be reviewed for best results. Finally, checklists for IT should be created to ensure that IT is following the policies and procedures defined by leadership.
3. Implement the ISCM program
Implementation simply is executing the plan and program established in Steps 1 and 2. This should be performed in a checklist format that is consistent with the strategic policies and procedures defined by organizational leadership. The IT representative should sign and date the checklist to inform management who performed the work and when. This provides assurance and accountability for implementation.
4. Analyze and Report the findings of your program
The first data collection serves as a security baseline for where the organization is currently. Comparisons back to the baseline over time can indicate when abnormal activity or changes are occurring within the organization. Gradually, the baseline can grow to become more informative.
As abnormalities appear in the reporting and analysis process, those findings are submitted to authorities according to the defined policies and procedures for them to make decisions regarding the risks associated with that abnormality. Early on in this process, there can be a lot of noise generated; but as the reporting and analysis window grows, IT can identify abnormalities with greater accuracy.
5. Respond to those findings
Knowing how to respond to security events is more of an art than a science, because every environment is different. Every organization, even within the same industry, has a different approach and perspective on risk tolerance and mitigation. The policies and procedures created in the strategic phase of the ISCM will guide IT on how to respond appropriately to security events.
There will be times when a security event exposes a weakness overlooked in the initial strategic planning process. This should be expected. Technology is ever-changing. Hardly ever is the first attempt perfect. There is not a perfect approach to security, so when a weakness is detected, avoid the temptation to point fingers and assign blame. Then, proceed to step 6.
6. Review and Update your ISCM strategy and program
As stated above, going through the exercises of analyzing and reporting will inevitably expose weaknesses in your ISCM. The important point here is that the organization is growing and maturing with relation to its security posture and awareness. What are new ways to detect abnormalities which would be more efficient? What new ways has IT discovered to monitor for security-related abnormalities? What new policies and procedures could be adopted to mitigate the associated risk of this new weakness? These questions, and ones like them, can help you refine your ISCM over time.
Here is another helpful illustration from NIST 800-137 for how this process should look:

Conclusion:
Creating and performing an ISCM is something like learning any new skill. It will take a while before you become adept at identifying security risks within your organization and mitigating them to an acceptable level. At first, it can feel awkward, and it’s easy simply to procrastinate. The important thing is that you start and stick with it. Over time, you will grow and become more adept.
Sometimes, it’s helpful to have someone assist you in these exercises. That’s where TCS can help. We support and manage security for various regulated industries (health, finance, defense, local government, and beyond). We use that collective experience to create a unique, client-focused approach to security. TCS can work with you to grow your security posture over time by road-mapping solutions on a scheduled timetable and performing routine security assessments both to demonstrate your past growth and effectively plan for better security where weaknesses are identified. Contact us today, if you would like to know more about how TCS can assist your organization with its cybersecurity needs.
Note: This article was written from resources found at the following site: https://www.nist.gov/cyberframework/detect

 Thinkstock
Thinkstock iStock
iStock