Business Continuity Part 4
Pour the Coffee
Let’s put on a pot of coffee and roll up our sleeves for this one. We are about to get into the meat of the Business Continuity Plan and we will want to slow things down and focus on our business functions. The good news is when we are finished with today’s effort, we will complete Chapter 1 and be 40% finished with the Plan.
And if you have followed our guidance during the Pandemic, your company operations should be flexible in a variety of conditions due to adopting work from home solutions. This can include laptops, VPNs, IP phones, cloud applications and document storage, or other technologies that help extend your business functions outside of your brick-and-mortar environment. For TCS, this becomes a game changer and creates an almost seamless transition across all business functions to shift from the office to a home/remote office setup.
1.6 Risk Assessments

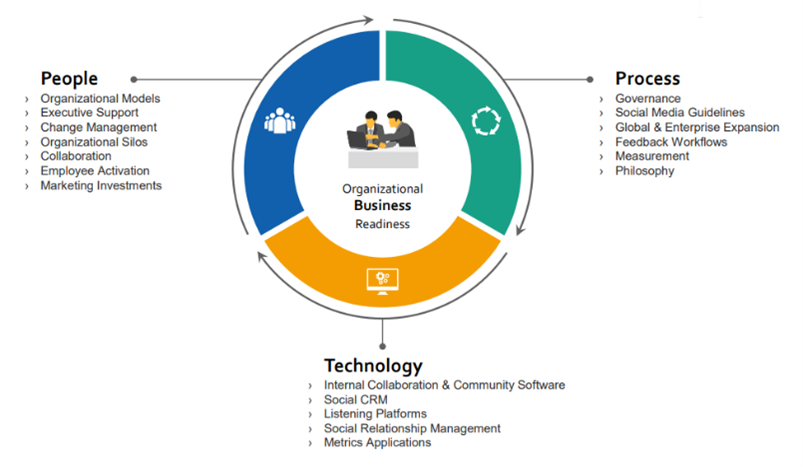
We will now document and score what threats may impact our People, Process, and Technology. As you can see from the screenshot above, we will assess/score the Probability of the threat, the Business Impact of that threat, and our ability to Control the threat. Each of these will be scored on a scale of 1 to 5, 1 being “Low”, “No Impact”, and “Good” respectively and 5 represents “High”, “High Impact”, and “Poor” respectively.
The tool provides a sample threat list like the one pictured below:

Also, an example of the Risk Assessment table is provided:

Take time to read through the list of threats and look at the examples on how you may score the threats, along with a summary of how the threat could be mitigated. Each organization will vary in the type of threats, the scoring, and how the threats are mitigated. This is where you want to spend some energy deliberating on this and work with your team to come up with a comprehensive list. This exercise could expose some areas where you may need to do more to beef up your continuity strategy.
TCS ended up with 13 different areas but most of them could be at least partially mitigated by defaulting to a work from home strategy. This may not be possible for all your team, especially if their job function is dependent on equipment or systems on premise. A helpful tip is to review the Houston County Pre-Disaster Mitigation Plan located here:
https://www.houstoncountyga.org/skins/userfiles/files/Houston%20Co%20PDMP%202020%20(Public).pdf.
This plan addresses many external threats common to our region and can inform your mitigation strategies or affect your scoring because some of these threats are being mitigated at a higher level already. There is no absolute right or wrong here and the important thing is that these threats are considered and addressed in some logical fashion that is appropriate for your business. A useful strategy I learned from attending the GBA Southern Operations and Technology School and by working with other Risk Management professionals is to rank order the threats by multiplying each of the 3 score areas (Probability x Impact x Control). This will give you a composite score for each threat category ranging from 0 to 125. Understanding these threats as a ranked list can help prioritize spending to further reduce risk if there are gaps in your capabilities. Of course TCS is available to consult with you regarding your business technology strategy to better align with your mitigation plans.
1.7 Business Impact Analysis Summary
In this step we want to describe how you determined what to include and leave out of your risk analysis. What business functions, processes, and interdependencies did you consider? This does not have to be perfect, and it will likely change over time as you revise your plan, but we want to get a basic statement down on paper and go from there. Part of our BIA statement included factors studied by Houston County in their plan and we made certain assumptions as a result. For example, the frequency of tornadoes and floods are addressed in their document.

In the BIA Summary example pictured above, you will see how the Plan will document your different business units and its functions along with the associated manager, processes, and related risks. Additionally, you will want to determine the maximum time you will allow for a critical function to be down, and the daily revenue loss caused by the loss of business function. The Recovery Time Objective (RTO) will inform how you prioritize your resources before and during a disaster to recover these functions. Defining the RTO and RPO (Recovery Point Objective) also helps IT know what business continuity and disaster recovery (and backup history) you need to recover business functions, including the information systems and data. The lower (in number of days or hours) your RTO and the narrower your RPO, the more expensive the technology solutions will be to achieve the desired goals. This will be a calculated tradeoff between the capital and operational cost of the technical capability versus the likelihood and (financial or business reputation) impact of an event. This is a conversation to be had with your IT folks well before a disaster. It will not be helpful to have an undefined RTO only to discover recovering your data from the cloud will take days and you want that business system up in hours.
1.8 Business Continuity Strategy
In this section we want to describe, at a high level, the overall approach to maintaining continuity of your business functions. This will include basic details of a secondary site for temporary operations along with a map and contract information for that site.
1.9 Emergency Operations Center (EOC) Locations/Contacts
This section is straightforward. You will list each of your Emergency Operations Center locations, a named point of contact, and a phone number for each site. This could be one site, or you may define multiple. It is a good idea to have a prearranged agreement with another organization if they have space to accommodate your business continuity team in an emergency. This could be a reciprocal agreement.
1.10 Alternate Site Locations and Contacts
You will want to complete a similar list for alternate sites for business operations. This could be the same as your Emergency Operations Center or a different location. If you have an offsite storage facility, you will want to document that in the appropriate section as well.
1.11 Organizational Chart
During a disaster is not the time to try and figure out who all works where and reports to whom. Take the time now, if you do not have one, and document the business functions, management, and staff across your business. If you have this already, simply copy and paste image into the space provided.
1.12 Team Descriptions and Organization Chart
If your business continuity team will differ in personnel or structure to your org chart, it will be helpful to create a similar chart to define your Business Continuity Organization structure. An example is provided below; however, this is overkill for TCS being a smaller company, so we opted just to keep our regular org chart knowing the CEO and COO will quarterback the continuity and recovery efforts while Service is busy supporting our clients. Your mileage may vary.

1.13 Emergency Response Plan Summary
You will summarize the key elements of your Emergency Response Plan in this section. This plan is separate and distinct from the Business Continuity Plan, although there is overlap. The BPC will focus primarily on recovery and mitigation and the ERP will focus on preparedness and response.
Okay, time to hit the pause button until next week. From here we will document various teams and essential lists that are critical to business operations. This will take us into Chapter 2 of the tool/plan – Critical Business Information. For those who like checking boxes, here is where we are until we take this up again. Good progress!












