Chapter 2 – Critical Business Information
Hopefully we have all recovered from the somewhat heavy lifting of doing the risk assessment and business impact analysis. In this chapter we will document several different lists that may be needed during a business continuity scenario. Most of this information you will already have in various systems like a Customer Relationship Management (CRM) or accounting/billing system. And it will be good to have all of this captured in one document just in case. For our purposes, TCS will define the following teams: Management, Service, Human Resources, and Finance. You could start with a similar structure, depending on your organization, and adjust later if needed.
2.1 Team Call List
In this section we will document the home and work contact information for each employee under his or her respective team. Easy peasy.
2.2 Team Task List
Now we will define, for each team, a set of tasks to be performed throughout the duration of the business continuity event. This is a who/what/when list for each department in our case. Think through your business “People, Process, and Technology” structure again and identify the essential tasks to be performed, deprioritizing the non-essential tasks if necessary. And, yes, I intend to get maximum use of our PPT graphic since this concept keeps coming up in our discussion.
2.3 Team Action Plan
The Action Plan will feel somewhat redundant to the Task List you just created. The way the tool (and sample text) treats this section is defining the Continuity-specific responsibilities and tasks on a per-team and per-site basis where the previous list dealt with the continuation of routine work functions. It is likely some personnel will have more tasks defined in one list than the other depending on the specific role and delegated tasks. Some (managers in the case of TCS) will coordinate more heavily on managing the continuity and recovery communication and coordination where our Service Team will remain mostly client facing. This is a little nuanced and the most important thing is the essential tasks are defined in your plan in one place or the other.
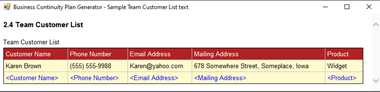
2.4 Team Customer List
Now we will create a list of our key customer contacts. Since the app provides a separate list for each team, you may want to separate a billing contact versus other contacts. For TCS this includes a list of our technical points of contact and billing contacts. If you have defined a Management team like we have, then you could also list key management contacts in that section separate from your primary contacts.
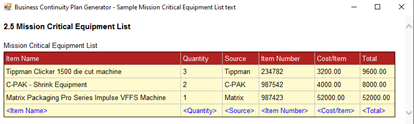
2.5 Team Critical Equipment List
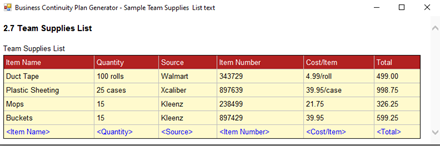
Continuing with our critical lists…we want to document essential equipment. Think through what items you might need to keep your department going and enter the item, quantity, vendor source, item number, per item cost, and total cost for each row. As before, the list will be broken down by department. It would be a good idea, if you have a redundant site or an agreement to use another facility, to keep enough inventory stored to provide quick access to essential equipment. Otherwise, try to identify a local vendor where you would acquire the equipment with short notice.
2.6 Team Software List
Now we will create a list of software required to run your business. If you are leveraging hosted or cloud software, then it may be possible to operate with minimal critical requirements for downloadable software. In fact, a key business strategy would be to move in that general direction. For example, if you are using Microsoft 365 with hosted email and cloud document storage, perhaps you could get away with using a Chromebook (or any devices with a browser) and get by until your normal setup could be fully restored. Another effective solution, especially for line of business applications that are not yet cloud-ready, is to use a Terminal Server for remote access to these applications. TCS offers a cloud backup solution where the Terminal Server can be run virtualized in the cloud until the on-premise servers and data are be rebuilt. We are aiming for the lowest cost minimum functionality needed to run the business and the trend is moving in this direction, so it’s worth checking with your IT company and software vendors to assess these capabilities before a disaster. In fact, I wrote my first article for TCS on this subject a little over a year ago: Strategy: Turning Your Business Inside Out. While not ideal, my computing requirements and our business systems would (by design) allow me to operate on a Chromebook with no additional installed software. My business phone number could be forwarded to my cell, and voila!
2.7 Team Supplies List
Now is time for me to admit having a dark sense of humor…it’s true! When I read the provided example Supplies List, I couldn’t help but wonder what kind of bad day DHS was aiming for when they put together this list…
This reads like items needed after a zombie apocalypse. I would add shovel and rope and consider my list complete, but I digress 😊
But you get the drill by now…put together a list of supplies you may need and hope your rainy day is less dramatic than what DHS thinks you will need. And if you think I’m making this up, Google “CDC” and “Zombie” and see what comes up.
2.8 Team Telecommunications List
The reality for TCS is we are small enough where most of these lists can be done in one place. We just don’t need 1000 items in 20 different department lists, but your mileage may vary. Simpler is better in my opinion.
For Telecommunications, we want the vendor, account number, support number, and the name and email of your point of contact – most likely an account representative.
My goal is to adopt StarLink satellite Internet, at least as a secondary provider, as soon as service is available in our area. This would make a great backup connection that doesn’t rely on ground-based cabling/fiber infrastructure. As Elon Musk says, “Plug in socket, point at sky. These instructions work in either order.” How about that for getting your Internet access back up and running post haste?!
2.9 Team Vendor List
Critical vendors. Document them.
2.10 Team Vital Records List
This list includes backups…you are backing up to the cloud, right?! Critical data, intellectual property, contracts, diagrams. The best plan here is to have everything in digital form then ensure you have local and cloud copies/backups of this data. And when we say backup, we mean geographically redundant storage…not keeping a data tape in a separate room from your server.
<soapbox>If your technology vendor cannot explain in simple terms how they know your backups are executing and the data integrity is validated daily, then it may be time to shop around for someone who gets this.</soapbox>
Time to pat yourself and your team on the back! By my count we are 56.8% complete with our plan. In Chapter 3 we will walk through Plan Administration and Maintenance. This next section is the catalyst that enables companywide adoption through training and awareness. It also will develop the process for ongoing plan maintenance, thus not becoming an outdated binder on the shelf that is no longer relevant to your business.
TTFN!